Creating an endpoint policy for S3 buckets allows you to control access to those buckets.
In this lab, I will provide steps by steps of Creating an endpoint policy for S3 buckets that allows you to control access to those buckets from your VPC using an interface VPC endpoint.
Background
A VPC endpoint for S3, also known as an Interface Endpoint, enables you to connect your Amazon Virtual Private Cloud (VPC) directly to S3. It allows you to access S3 buckets and objects privately from within your VPC, without needing to traverse the public internet.
An endpoint policy for an Amazon S3 bucket is a set of permissions that define which actions are allowed or denied for requests coming from within an Amazon VPC via the VPC endpoint. When you create a VPC endpoint for S3, you can attach an endpoint policy to control access to the S3 bucket through that endpoint.
Prerequisite
For this project, you need an AWS account. Set up a Free-Tier account www.aws.amazon.com/free.
Scenario
You are a cloud engineer in a project. For security reason, your company asked you to control access for several S3 buckets by using a gateway endpoint to allow access to trusted buckets.
Solution
I will create an endpoint policy for trusted s3 buckets.
Step 1: Identify (or create) the VPC and S3 bucket
- Sign in to the AWS Management Console and select your preferred region.
- Identify the VPC in which you want to create the VPC endpoint.
- Note down the Amazon S3 bucket ARN (Amazon Resource Name) of the trusted bucket that you want to access through the VPC endpoint.
Cheat Sheet: If you don’t have VPC and S3 already, create a VPC (I made a lab about VPC previously here) and create a S3 bucket (read this article about how to create S3 bucket) .
Step 2: Create a VPC Endpoint
- Navigate to the VPC console.
- In the VPC Management Console, click on “Endpoints” in the left navigation pane.
- Click the “Create Endpoint” button.
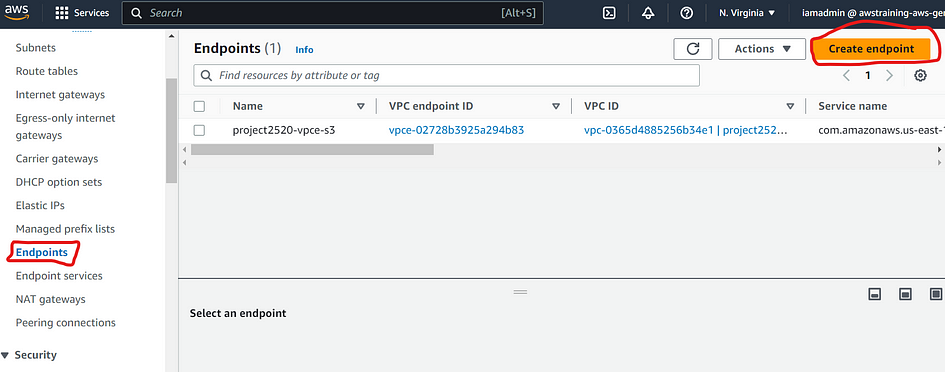
Cheat Sheet: There are three types of VPC endpoints — Interface endpoints, Gateway Load Balancer endpoints, and Gateway endpoints. Interface endpoints and Gateway Load Balancer endpoints are powered by AWS PrivateLink, and use an Elastic Network Interface (ENI) as an entry point for traffic destined to the service. Interface endpoints are typically accessed using the public or private DNS name associated with the service, while Gateway endpoints and Gateway Load Balancer endpoints serve as a target for a route in your route table for traffic destined for the service.
- In the “Create Endpoint” wizard, name the endpoint (it’s optional). Select “AWS Services” as the service category, and select S3 as service in the list below.
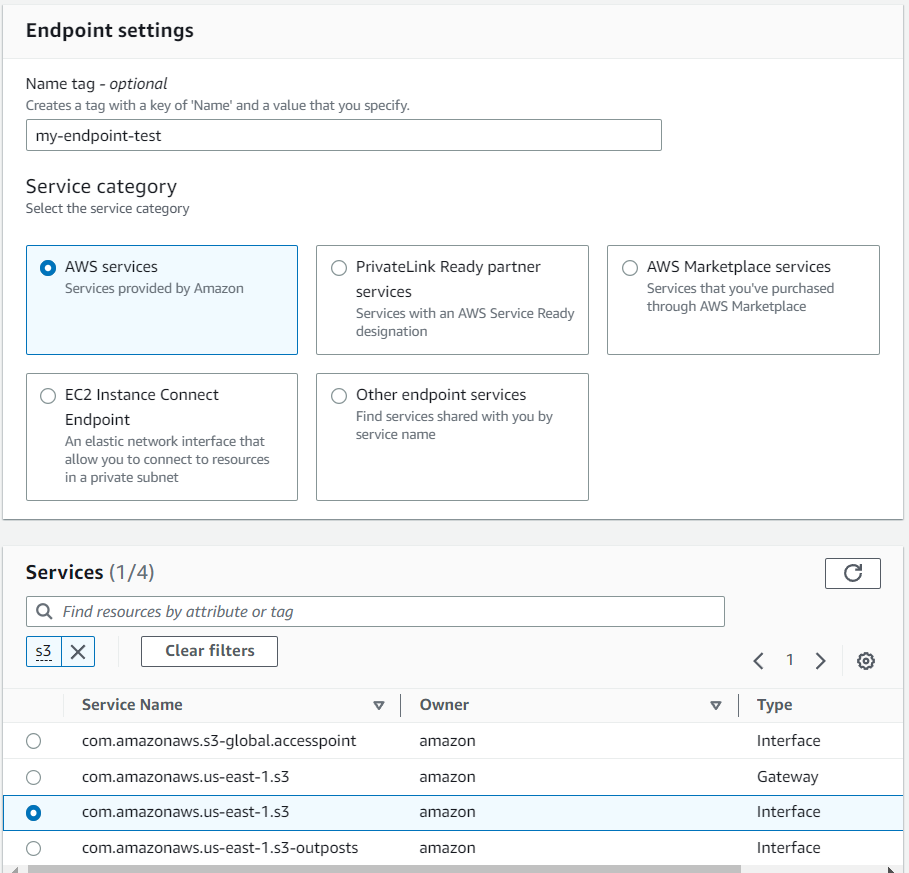
- Choose the desired VPC from the drop-down list.
- Select the subnet(s) in which you want to create the VPC endpoint.
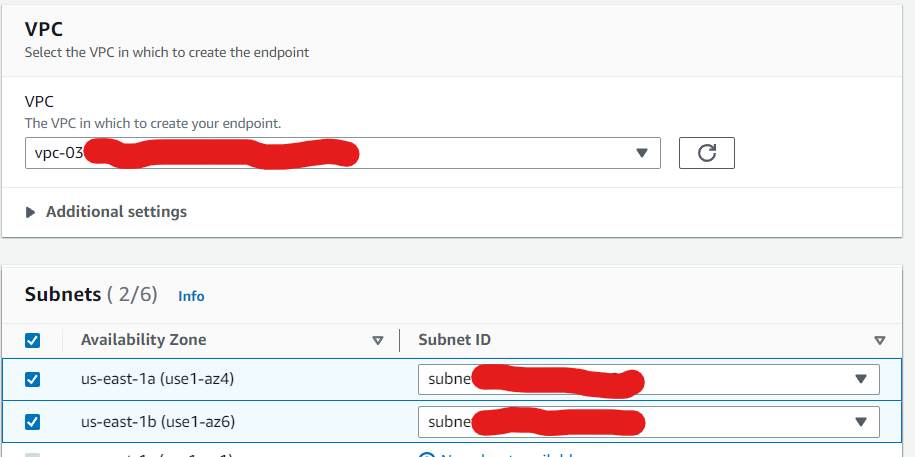
- Then select a security group.
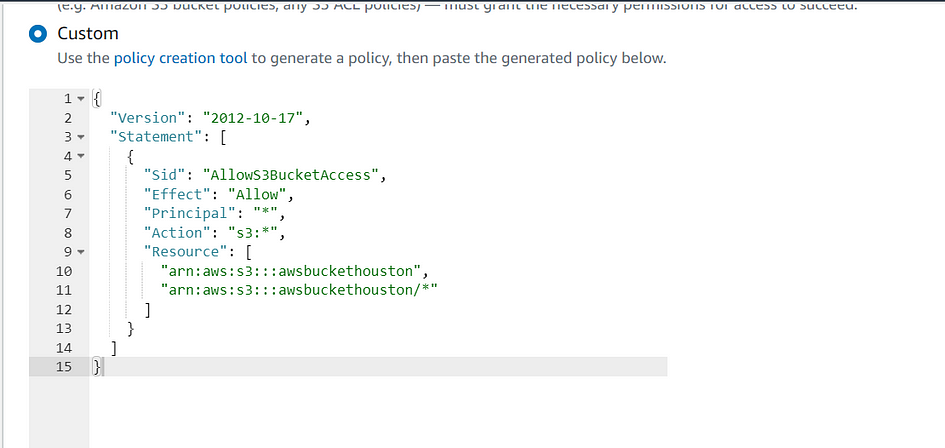
- In the “Policy” section, select “Custom” from the drop-down list.
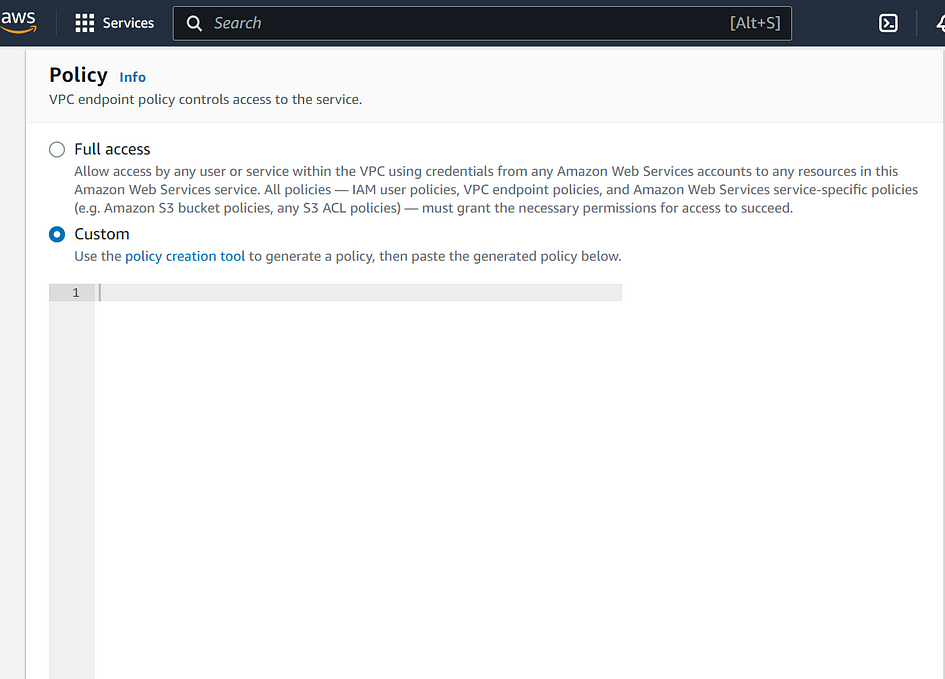
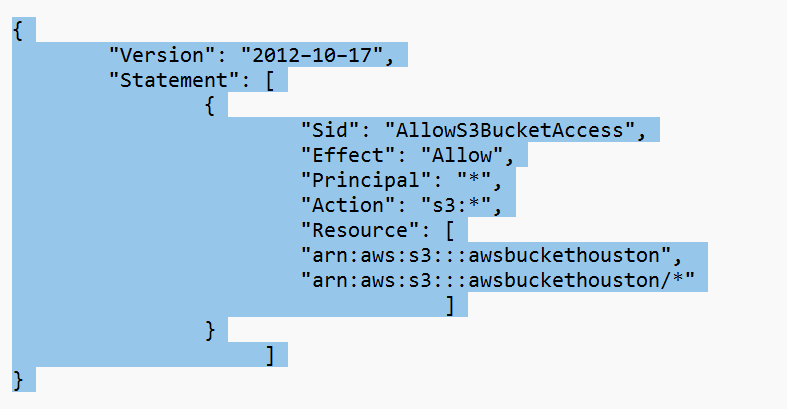
- In the “Policy Document” box, enter the JSON policy document that specifies the permissions you want to grant for the VPC endpoint. The policy should allow access to the trusted S3 bucket(s) by their ARNs.
In my case, I will give access to my S3 buckets. See the policy below:
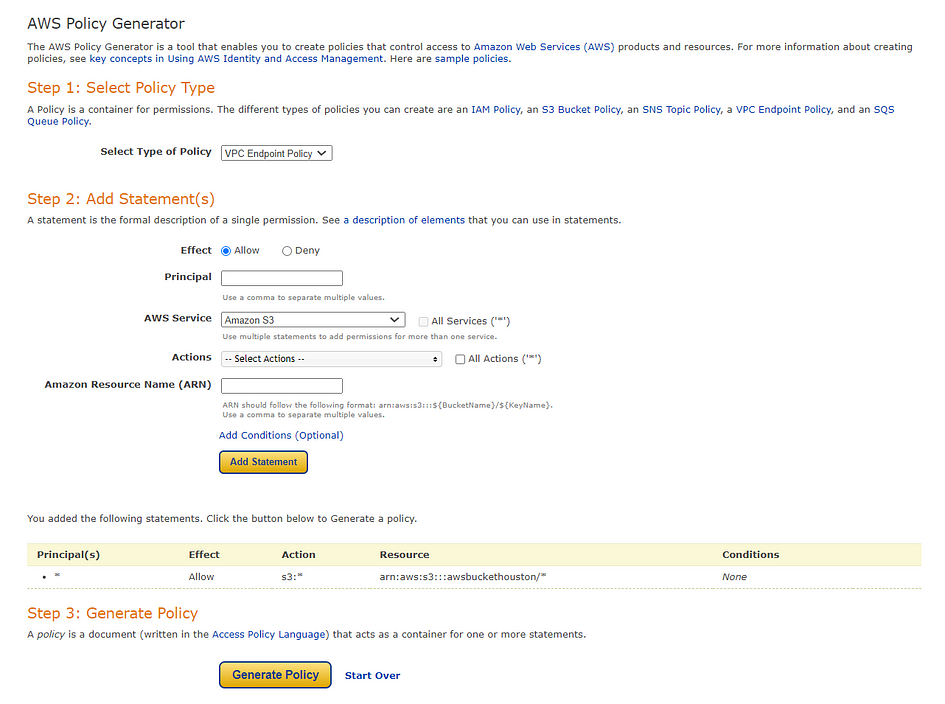
- (OR) You can use AWS policy generator to create one automatically.
- Review your settings and the policy document carefully to ensure they are correct.
- Click the “Create Endpoint” button to create the VPC endpoint with the specified policy.
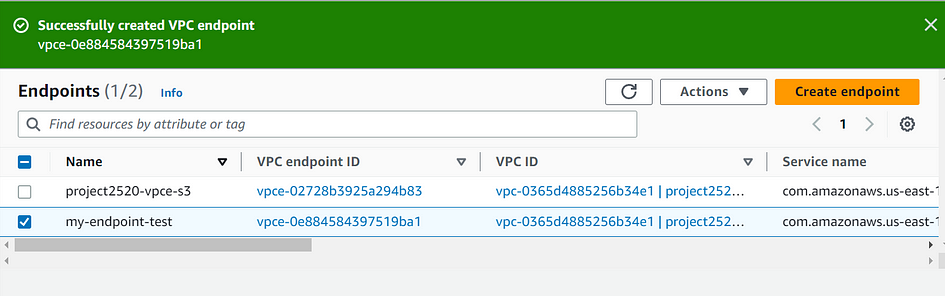
Step 3: Test the Endpoint
After creating the VPC endpoint, you can test access to the trusted S3 bucket(s) from within your VPC without going over the internet.
Test 1: AWS CLI
- Open a terminal or command prompt or connect to a Bastion host within the VPC.
- Use the AWS CLI to run a simple S3 command to list objects in a bucket
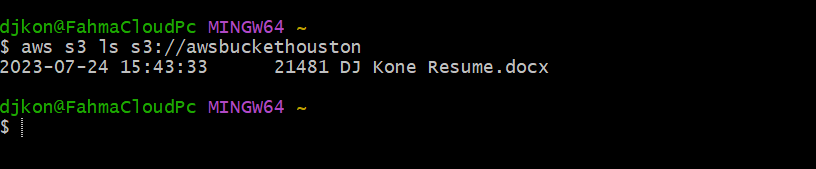
This test was successful. As you see, my resume is the only object in my S3 bucket.
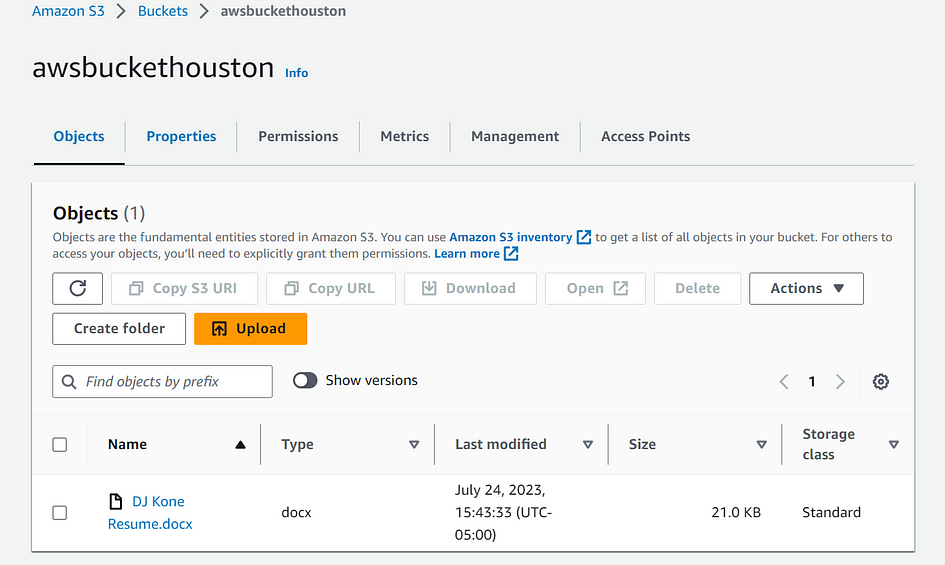
Test 2: Check AWS Console Connectivity
- Log in to the AWS Management Console using a machine within the VPC
- Navigate to the S3 service, and check if you can list objects, upload files, or perform other desired actions on your S3 buckets using the console. This test was successful also.
Cheat sheet: For the purpose of this lab, I used a policy that allows unrestricted access from any AWS account. In a production environment, you should customize the policy to grant access only to the specific AWS accounts or IAM users/roles that need access. Additionally, make sure to follow security best practices to protect your resources and data effectively.
Voilà! You know how to have created an endpoint policy for S3 buckets that allows you to control access to those buckets from your VPC using an interface VPC endpoint.
Thank you for reading and/or following along!


Leave a Reply